It may be even more concerning now with ai being fed your data as well. Major profiling and stuff.
2 posts were merged into an existing topic: MW and LW love fest
Theoretically. Hopefully.
This is not just for graphene OS but any AOSP rom.
Proof is in your own compiling of an OS yourself.
Have the source code yourself and do the damn thing or quit bitching.
Absolute trust comes from doing things yourself. Always. Nobody here is trying to stop others from doing that. But you’re dumber to let apps harvest your data vs a solution focused on preventing that because you’re too stupid to do it yourself.
Data is real and you’d be blind to not notice the differences between a regular store phone and this experience in your data safety.
Trust is still blind, but I’d rather trust my phone to small company than a big one when security is concerned. Smaller targets are harder to hit.
The fact y’all want to act all bad ass but refuse to even show your ability to root your phone or even unlock your bootloader’s makes me question the authenticity of your complaints. Just looks like a lot of talk from dudes with zero ability or willingness to participate in proving their ability and knowledge on the subject matter.
Oh you’re @Extractionperson5.0 ![]()
so you dont think the data can be read from different areas>? do you not think any intelligence agency can gain access to other data once they have access to the memory of the phone?
security is meant to be defeated. I still dont understand the concept of this phone. Especially built on the android platform.
Stopping 3 letter agencies are off the table probably. Example, This is for things like
Someone sends you a picture, it executes code and gains access to all things your gallery is privileged for.
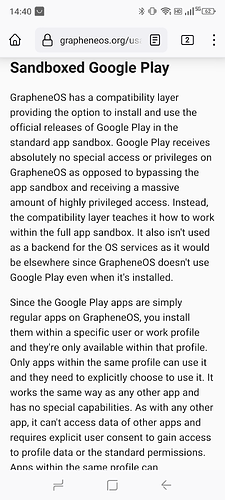
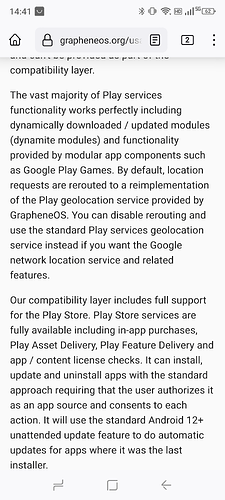
the baseband is isolated on all of the officially supported devices. Memory access is partitioned by the IOMMU and limited to internal memory and memory shared by the driver implementations. The baseband on the officially supported devices with a Qualcomm SoC implements Wi-Fi and Bluetooth as internal sandboxed processes rather than having a separate baseband for those like earlier devices.
Enabling Storage Scopes makes the app assume that is has all of storage permissions that were requested by it, despite not actually having any of them.
This means that the app can’t see any of the files that were created by other apps. The app is still allowed to create files and directories, same as any other modern app that doesn’t have any storage access permission.
The moment you put your device in developer mode is the moment you voided the warranty.
Js.
Nah that shouldn’t void the warranty, and as far at tmobile/verizon goes neither does unlocking the bootloader (on most phones), rooting and custom roms will usually void the warranty. On some phones you can flash back stock rom, relock the bootloader, and no one is the wiser.
I think Matt has clearly said although did not make it clear that this phone is meant more for companies/“entities” that are trying to keep their business confidential, then what it is for individuals in this industry. As far as Matt’s credibility goes, although I have never met him I have known him and spoke to him extensively for the past year or so and while we have not seen eye to eye on occasions he has thus far proven to be an honest guy on a much larger deal that he could have tried to be dishonest about and screw me but didn’t. If you worried about the feds listening to you then there is no smart phone that’s going to be safe (look up Pegasus exploit) from a government entity really wanting to know what you’re up to. But that concern is not one being shared with legal “entities” and as such this might be a good option for them (I don’t know enough about this phone to endorse it or to condemn it). I would say if you are in a position to supply a bunch of your employees with “secure communications” you should really look into this phone and who are the people who are truly involved then make a decision but not before, otherwise it’s just a bunch of bullshit talk.
Just my two cents worth.
15 posts were merged into an existing topic: Lukewarm being lukecold
Using a google phone will never be open source, because they took an open source processor and made closed source firmware for it. It just ain’t happening, period
Mostly read through the whole thread, enjoyed it thoroughly lol. I’m the chief architect of the SecurePhone by MLABS.
Some context, @BrotanicalMatt is correct that this is not our target market, but we’re happy to branch out where applicable. Our standard approach is to provide customized secure mobility solutions for organizations with 100 - 1000+ mobile users. We generally offer our baseline product as a private offering to interested individuals and organizations who do not meet the volume requirements for a custom build, customized software/app load, or other device modifications.
Since this is a private offering, please email contact@mlabsindustries.com for the password to our website. We request that you do not share it as we’ll have to change it if you do. Sidco’s code will still work for your discount.
To address some of the concerns voiced here… This device is not meant to be the most secure cell phone ever made. Ultra high security phones are immensely expensive and tightly controlled. Government agencies have them, but standard consumers cannot purchase them. Even if we were to make one, it would be unaffordable…custom hardware and chain of custody requirements for every piece of hardware, firmware, and software all add to the cost of the device. Not to mention all of the additional secure telephony enhancements needed to make something like that viable. There’s a very good reason why an ultra high security phone is typically $5000+ per device.
The intended use case of the SecurePhone is to provide a security and privacy enhanced mobility experience to large and/or high security organizations, especially those with BYOD or corporate phone policies. The utility of a standard smartphone + additional security. Additional flexibility is also gained as a result of increased control over your device, and is an added benefit for the more technical user.
For insight into our process, the device is shipped with a verifiable GrapheneOS image and receives OTA’s directly from the Graphene org. The app load and device configurations are standardized and automatically loaded after flashing. Since Android OS is based on Linux, and GrapheneOS is our starting point, we take an approach similar to RedHat with Linux (RHEL and CENTOS, for example) and pre-configure all devices for maximum privacy, security, and usability by default. While we offer customization and product support to our larger customers, smaller customers have access to the standard open-source product for their individual usage…effectively making a higher level of mobile security more accessible to the average consumer.
As for the concerns voiced about transparency and open-source. For the devices sold online from our website, the OS image comes directly from GrapheneOS with the only modifications being the configuration and app load. It’s unfortunately impractical to build an entirely open-source system since so much hardware, firmware, and software remains closed source for now…hopefully this won’t always be the case.
We’re presenting our best offer for a security and privacy enhanced device at a reasonable price. Nothing beats good OPSEC and a healthy amount of paranoia, but we’re confident this device has merit as an improvement to standard smartphones for personal privacy and security.
Happy to answer any other questions, I’m not on here often but I’ll check in at least once a week. For anything that you want to remain private, please use PGP. I’ll provide my public key on request.
How is the improvement comparable to the security capabilities you implied the ‘government agencies’ are in possession of for the purpose of stating a consumer standard?
This phone was advertised as a drug dealer phone here lol. That’s why people shit on the whole thing, me included.
Good on you guys for doing your thing, but what was being offered and what’s being said now are two very different things.
I missed that part, went back through the first half of the thread and didn’t see it anywhere. Who advertised it as a “drug dealer” phone?
23 posts were split to a new topic: MW and CR love fest
Thank you for posting.
But, what you and others have thus far shared is far from enough and doesn’t lend any credibility to your company. Open up your website for starters. When I first visited the URL your site was open. You only made it private after you stated getting heat from F4200 members. Otherwise, it sure looks like you’re a believer of “security through obscurity,” which, as you know, is doomed to fail.
While I have no dog in this fight, I do know a thing or three about OPSEC and computer/phone security. I would be happy to offer advise for you and the company to get back on track. First and foremost:
- Open up your website.
- Provide design docs.
- Pay for independent 3rd party security audit of your phone and build process (and then share the report after you fix the bugs and flaws they WILL find).
- Is your build process reproducible and done on an air gaped system? If not, work on that.
- Deal with Evil Maids.
For you and others reading, here are some of my comments on this phone and how @sidco 's involvement is concerning: